Although ransomware doesn't specifically target Microsoft 365 data, it can affect Exchange Online, Sharepoint Online and other cloud applications, as well as use Microsoft 365 to spread inside organizations.
Files encrypted locally can be synched to M365 Site/OneDrive
We've seen cases when ransomware encrypted local files on user desktop machines and the encrypted versions of the data were synched by the OneDrive application to Microsoft 365 cloud.
There is no evidence, however, that the criminals intended or cared if the encrypted files are uploaded to the cloud.
OneDrive application normally uploads data to Microsoft 365 at around 2MB/sec, which is 10-15x slower than the speed of data encryption operations on local machines. This often means that only a small share of encrypted data is synched from local machines to Microsoft 365 cloud before the attack is discovered.
Cloud upload speed is too slow to encrypt Microsoft 365 (SharePoint and OneDrive) data at scale.
When encrypted files get uploaded to OneDrive accounts or SharePoint sites, they can usually be recovered using the standard Microsoft 365 versioning (see section 3 for more details on M365 built-in anti-ransomware tools).
Microsoft 365 can be a point of entry for ransomware
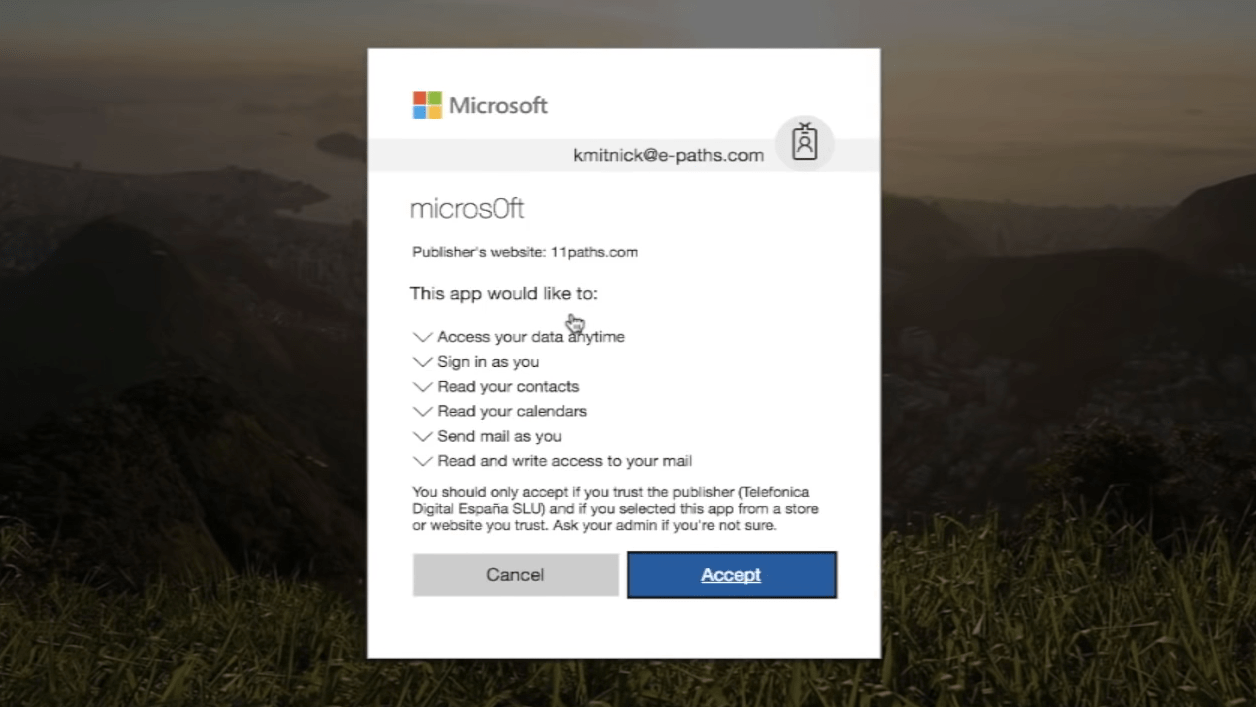
Email phishing in one of the most important ransomware attack vectors. Criminals often use Microsoft 365 Exchange Online (along with other email services) to infect their victims by sending messages with infected attachments or links to malware.
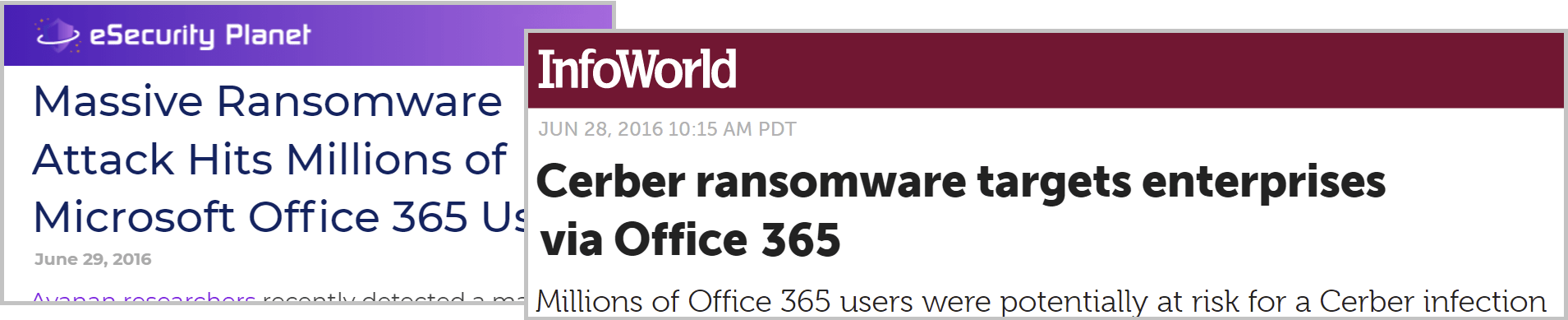
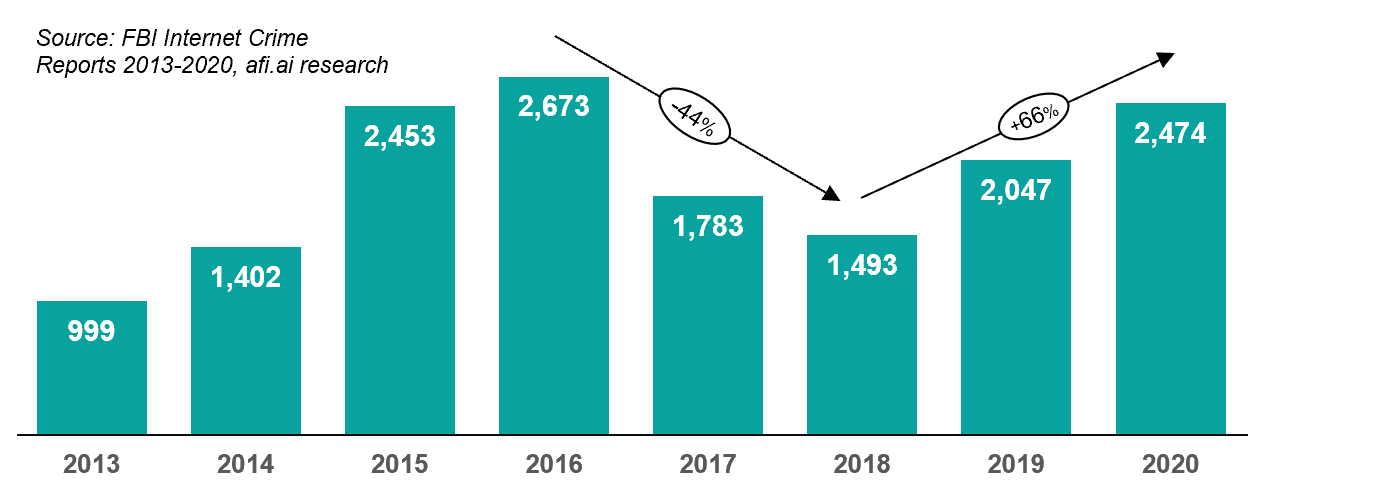
Cerber ransomware is a notable example where attackers focused on Microsoft (Office) 365 users to deliver phishing emails. In 2016 Cerber infected multiple enterprises by sending infected email attachment that was able to bypass the built-in Exchange Online filtering, so users who opened the attachment infected their local machines.
Cerber ransomware uses Exchange Online to penetrate networks; but it isn't focused on Microsoft 365 or Exchange data

Importantly, Cerber and other similar strains use Exchange Online only for the initial infection. The ransomware doesn't attempt to encrypt Microsoft 365 data itself. It instead spreads locally within infected organizations and encrypts on-premises data sources.
Microsoft 365 help ransomware spread within organization
After infecting the first machine (via Exchange Online or another attack vector), ransomware spreads further within the organization - this process is termed "lateral movement".
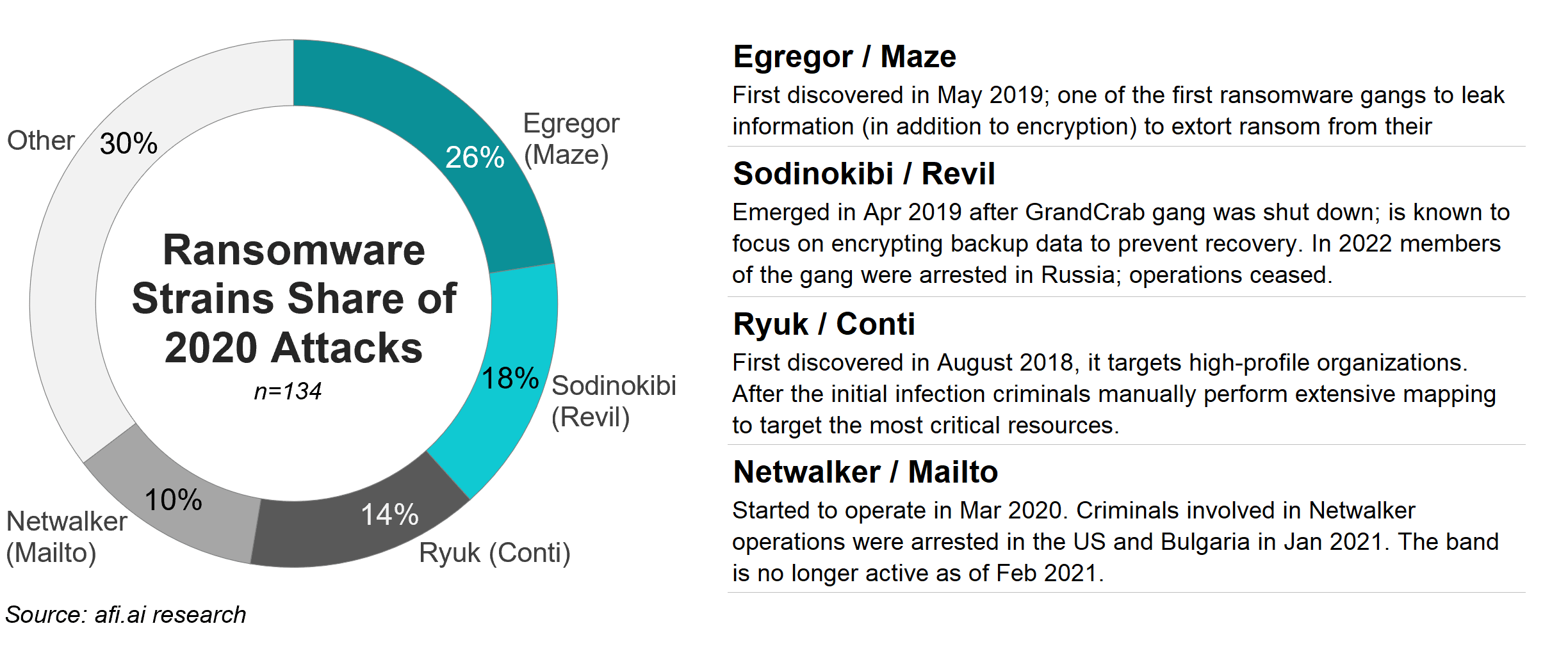
Most ransomware strains rely on the following ways to spread:
- Harvesting credentials and passwords stored on the infected machine(s) in order to access other computers
- Network scanning to identify & prioritize critical data sources to target
- Exploiting local network protocols vulnerabilities to attack other local machines
In addition, ransomware may plant infected files (including Microsoft Office documents) to local file sharing servers and to SharePoint Online sites - if ransomware has access to a machine that is synched to SharePoint using OneDrive application.
However, the method of ransomware propagation using shared file servers is slower and less reliable than harvesting credentials or exploiting network protocols/software vulnerabilities. Planting infected files requires users to notice and open them on machines that run old/vulnerable OS versions that will not detect ransomware.
To sum up, SharePoint Online may be used to spread ransomware within organization (as a secondary lateral movement option), in case infected files are synched from an infected machine to a SharePoint site.
Can ransomware be executed in Microsoft 365 cloud?
It is important to note that Microsoft 365 itself cannot run or execute ransomware. An infected file must be opened on a local machine (Windows/Linux/Mac, etc) to be executed.
SharePoint Online and other Microsoft 365 apps can only act as storage media for ransomware executable files. Ransomware can only perform encryption & infect systems when it's downloaded and opened on a server or a user machine.